Secure your Data with Inferno🔥, Use Code: INFERNO100
SLOW#TEMPEST: Uncovering a Covert Cyber Espionage Campaign Targeting Chinese-Speaking Users
highly organized cyber espionage campaign dubbed SLOW#TEMPEST, which has been targeting Chinese-speaking users through sophisticated phishing tactics. The attackers leverage malicious ZIP files and advanced exploitation tools like Cobalt Strike to infiltrate Windows systems, establish persistence, and move laterally undetected. With a strategic focus on Chinese business and government sectors, the campaign utilizes innovative methods such as DLL side-loading, privilege escalation, and network reconnaissance to maintain long-term access and evade detection.
DEVELOPMENT AND ECONOMIC THREATS
Phillemon Neluvhalani
9/2/20243 min read
Chinese-speaking users are currently the target of a "highly organized and sophisticated attack" campaign, which is believed to be leveraging phishing emails to infiltrate Windows systems with Cobalt Strike payloads, according to Securonix researchers Den Iuzvyk and Tim Peck. The campaign, dubbed SLOW#TEMPEST, appears to be a highly covert operation that has not yet been attributed to any known threat actor.
Attack Overview
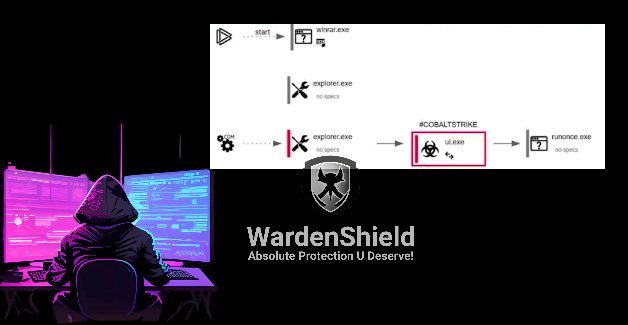
The attack begins with the distribution of malicious ZIP files, which, once unpacked, activate a multi-stage infection chain culminating in the deployment of a post-exploitation toolkit on compromised systems. These ZIP files contain a Windows shortcut (LNK) file disguised as a Microsoft Word document named "违规远程控制软件人员名单.docx.lnk," roughly translated as "List of people who violated the remote control software regulations." This file serves as a conduit for the attack by launching a legitimate Microsoft binary, "LicensingUI.exe," which uses DLL side-loading to execute a malicious DLL, "dui70.dll." Notably, this is the first documented instance of DLL side-loading via LicensingUI.exe, highlighting the campaign's innovative nature.
Infection and Persistence
The attackers reportedly managed to move laterally, establish persistence, and remain undetected within the targeted systems for more than two weeks. The malicious DLL, a Cobalt Strike implant, provides persistent and stealthy access to the infected host while connecting to a remote command-and-control (C2) server at "123.207.74[.]22." This server, hosted by Shenzhen Tencent Computer Systems Company Limited in China, reinforces the campaign's connection to Chinese infrastructure.
The Cobalt Strike implant enabled the attackers to carry out a range of hands-on activities, such as deploying additional payloads for reconnaissance and setting up proxied connections. A scheduled task is also created to periodically execute a malicious executable named "lld.exe," which can run arbitrary shellcode directly in memory, thereby minimizing disk footprint and evading detection.
Advanced Privilege Escalation Techniques
The attackers further demonstrated their sophistication by leveraging the built-in Guest user account, typically disabled and minimally privileged, to maintain access with minimal detection. They manually elevated this account's privileges by adding it to the administrative group and setting a new password, effectively transforming it into a powerful backdoor that allows ongoing access with little scrutiny.
Leveraging Advanced Reconnaissance
Once inside, the threat actors moved laterally across the network using Remote Desktop Protocol (RDP) and credentials extracted via the Mimikatz password extraction tool. The attackers then set up remote connections back to their C2 server from each compromised machine, allowing them to maintain a foothold within the network. During the post-exploitation phase, they executed numerous enumeration commands and employed the BloodHound tool to perform Active Directory (AD) reconnaissance, exfiltrating the results in a ZIP archive.
Insights and Connections to China
The campaign's complexity is underscored by its methodical approach to initial compromise, persistence, privilege escalation, and lateral movement across the network. All the C2 servers identified in this attack are hosted in China, and a majority of the attack artifacts have Chinese origins, suggesting a strong link to a China-based entity or group.
Despite the lack of direct evidence connecting this campaign to a known Advanced Persistent Threat (APT) group, Securonix researchers believe it to be orchestrated by a highly experienced threat actor. The use of advanced exploitation frameworks like Cobalt Strike, coupled with other post-exploitation tools, points to a seasoned actor with a deep understanding of attack strategies and stealth tactics.
Strategic Implications
The use of Chinese-language lures, such as the Word document disguised as "List of people who violated the remote control software regulations," suggests that the attackers are targeting specific Chinese business or government sectors. These sectors are likely to employ individuals familiar with or subject to "remote control software regulations," making them prime targets for this campaign.
Moreover, the campaign's use of DLL side-loading, advanced privilege escalation methods, and sophisticated post-exploitation tools highlights a growing trend among cybercriminals toward more covert and persistent attack strategies. This campaign also reflects an evolution in attack tactics, where threat actors increasingly leverage legitimate system tools and binaries to evade detection and complicate attribution.
This is a highly targeted and sophisticated cyber espionage campaign that leverages a combination of social engineering, novel exploitation techniques, and advanced post-exploitation frameworks to achieve its objectives. While the exact identity of the threat actor remains unknown, the evidence points to a highly capable and experienced group with significant resources and expertise. The campaign serves as a stark reminder of the growing sophistication and persistence of cyber threats, particularly those aimed at specific geopolitical regions or sectors.


