🕵️♂️Get Unbeatable deals across all products!🚀
Securing Web3: A Comprehensive Guide to Protecting Decentralized Systems
Securing Web3: A Comprehensive Guide to Protecting Decentralized Systems" explores Web3 security in the evolving digital landscape. Learn how to safeguard blockchain, smart contracts, dApps, cryptographic wallets, and decentralized governance against emerging threats. This guide covers real-world risks, best practices, and cutting-edge tools to enhance Web3 security, ensuring robust protection for decentralized technologies. Ideal for developers and users navigating Web3's unique challenges.
CYBERSECURITYEVOLVING TECH
Phillemon Neluvhalani
5/14/20254 min read
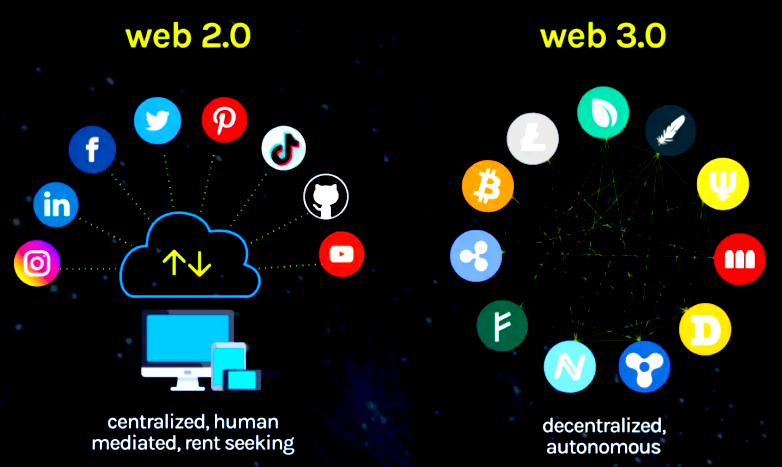
Web3 is often called the next big step for the internet—and for good reason. Built on decentralized technologies like blockchains, smart contracts, and peer-to-peer networks, it promises more control, transparency, and resilience for users. But with that promise comes a whole new wave of security challenges.
Unlike traditional Web2 systems, Web3 puts much of the security responsibility into the hands of developers, users, and infrastructure providers. The decentralized nature that makes Web3 so powerful also opens up new vulnerabilities. In this guide, we’ll break down the key components of Web3, common threats you need to watch for, and practical steps to make this emerging ecosystem safer for everyone.
What Exactly Is Web3—and Why Does It Matter for Security?
At its core, Web3 is a decentralized version of the internet, where users interact directly with applications (called dApps) through blockchain networks—often without any middleman.
Here’s a quick breakdown of what makes up the Web3 stack:
Blockchains: Distributed ledgers like Ethereum, Solana, or Binance Smart Chain that record transactions transparently and immutably.
Smart Contracts: Pieces of code that automatically execute agreements when certain conditions are met.
dApps: Decentralized apps that run on blockchains using smart contracts and user interfaces.
Crypto Wallets: Tools like MetaMask or Ledger that let users store and manage their private keys.
DeFi Platforms: Decentralized finance tools for lending, borrowing, or trading—without needing a bank.
NFTs: Unique digital assets tied to blockchain ownership, used in art, gaming, and collectibles.
While Web3 removes many centralized points of failure, it also means you can’t just “call IT” when something goes wrong. Let’s look at the common threats first.
The Most Common Threats in Web3 Today
Smart Contract Bugs: Exploitable flaws in the code that powers dApps and DeFi platforms.
Private Key Theft: If someone gets your private key, they control your assets. Period.
Phishing Scams: Fake websites and social engineering tricks to steal credentials or approvals.
Protocol Weaknesses: Design flaws in blockchains or consensus mechanisms.
Front-End Attacks: Compromised dApp interfaces that trick users into unsafe actions.
Economic Exploits: Like flash loan attacks or manipulating governance votes in DAOs.
1. How to Secure Smart Contracts
Smart contracts are the lifeblood of Web3, but they’re also a favorite target for hackers. In 2023 alone, over $3.7 billion was lost due to DeFi hacks—most of them linked to smart contract flaws.
✅ Smart Contract Security Best Practices:
Use Proven Frameworks: Stick with battle-tested tools like OpenZeppelin for Ethereum-based contracts.
Keep Code Clean and Modular: Simpler code = fewer bugs. Break large contracts into smaller pieces.
Set Permissions Wisely: Use access control mechanisms like Ownable or AccessControl.
Sanitize Inputs: Never trust user input. Validate everything.
Add Timelocks for Governance: Delay major changes to give the community a chance to respond.
Avoid Dangerous External Calls: If you must call external contracts, follow the Checks-Effects-Interactions
pattern.
🔍 Auditing and Testing:
Formal Verification: Use tools like Certora to mathematically prove contract correctness.
Test, Test, Test: Frameworks like Hardhat or Foundry help catch edge cases before deployment.
Bug Bounties: Platforms like Immunefi let white-hat hackers help find bugs—for a reward.
Hire the Pros: Audit firms like Trail of Bits or ConsenSys Diligence can help spot vulnerabilities you miss.
2. Securing Crypto Wallets
Your wallet is your front door to Web3. If someone gets in, it’s game over.
🔒 Wallet Safety Tips:
Go Hardware: Use Ledger or Trezor to store keys offline.
Multi-Sig for High Stakes: Tools like Gnosis Safe let you require multiple signatures for transactions.
Protect Your Seed Phrase: Never store it online or share it. Use cold storage.
Stick with Trusted Wallets: Download MetaMask or Trust Wallet only from official sites.
Enable 2FA: Especially for exchange accounts—use apps, not SMS.
Monitor Activity: Use blockchain explorers to spot unusual behavior early.
⚠️ Avoiding Phishing Scams:
Check URLs: Always verify the site you’re visiting. One typo can cost you everything.
Limit Approvals: Revoke unused token permissions with tools like Revoke.cash.
Educate Yourself: Stay up to date on the latest scam tactics. If it feels rushed or urgent—it’s probably a scam.
3. Securing dApps from Front to Back
Most people interact with Web3 through dApps. That means securing both the blockchain code and the user interface.
💻 Front-End Security:
Host on decentralized platforms like IPFS or Arweave.
Prevent XSS by sanitizing input and using proper headers.
Use vetted libraries like Web3.js or ethers.js for wallet interactions.
Keep your dependencies updated. Use tools like Snyk to catch known issues.
🔐 Back-End + API:
Rely on reputable oracles (e.g., Chainlink) for off-chain data.
Implement rate limits to prevent DoS attacks.
Monitor with tools like Forta or OpenZeppelin Defender for suspicious activity.
4. Locking Down the Blockchain Layer
Smart contracts run on top of blockchain protocols—but those base layers need protection too.
📦 Protocol-Level Tips:
Secure Consensus: Whether it’s PoS or PoW, guard against 51% attacks and validator collusion.
Node Hardening: Use firewalls and DDoS protection. Services like Infura help with reliability.
Governance Controls: DAOs should prevent takeovers by limiting voting power or using quadratic voting.
⚠️ Cross-Chain Risk:
Bridges like Wormhole or Multichain have lost billions to attacks. To protect them:
Use multi-sig or MPC to approve bridge transactions.
Audit bridge contracts thoroughly.
Watch bridge activity in real-time for red flags.
5. Battling Economic and DAO-Based Exploits
🏦 DeFi Defense:
Prevent flash loan exploits with circuit breakers and oracle safeguards.
Secure your liquidity pools. Stick with audited protocols.
Stress-test economic models under extreme conditions.
🧠 DAO Governance:
Avoid token hoarding by whales. Limit voting power concentration.
Use timelocks on all major proposals.
Keep governance contracts audited and simple.
6. Tools and Tech That Are Changing the Game
Web3 security is evolving fast. Here are some tools worth exploring:
Decentralized Identity (DID): Services like uPort let users control their identity without a password.
Zero-Knowledge Proofs (ZKPs): Projects like zkSync or StarkNet bring privacy and scalability.
AI Monitoring: Tools like Forta use machine learning to detect strange behavior in real-time.
Insurance Protocols: Platforms like Nexus Mutual offer protection against smart contract failures.
Social Recovery Wallets: Argent lets users recover accounts without needing a seed phrase.
7. The Human Side of Web3 Security
Even the best code won’t save us if users don’t understand the risks.
Teach Security Basics: Help users recognize scams, protect their wallets, and verify transactions.
Encourage Bug Reports: Reward people for finding and responsibly disclosing issues.
Be Transparent: Publish audits, disclose incidents, and share your security roadmap.
Final Thoughts: Security Is a Team Sport in Web3
Web3 gives us a chance to reshape the internet. But that vision only works if we take security seriously—from smart contracts and wallets to protocols and governance.
Developers: Build with security in mind. Use audits, test rigorously, and follow best practices.
Users: Protect your private keys like your life depends on it—because financially, it might.
Communities: Share knowledge. Promote transparency. Support ethical security research.


