Secure your Data with Inferno🔥, Use Code: INFERNO100
Cybersecurity Mesh Architecture: Future-Proofing Enterprise Security in a Decentralized World
This article, explores the innovative approach of Cybersecurity Mesh Architecture (CSMA) in modern cybersecurity. It explains what CSMA is, how it differs from traditional security models, and why it's crucial for protecting distributed digital infrastructures like cloud environments and IoT devices. The article outlines the benefits of CSMA, including enhanced threat intelligence, adaptive security controls, and improved scalability.
Phillemon Neluvhalani
2/16/20253 min read
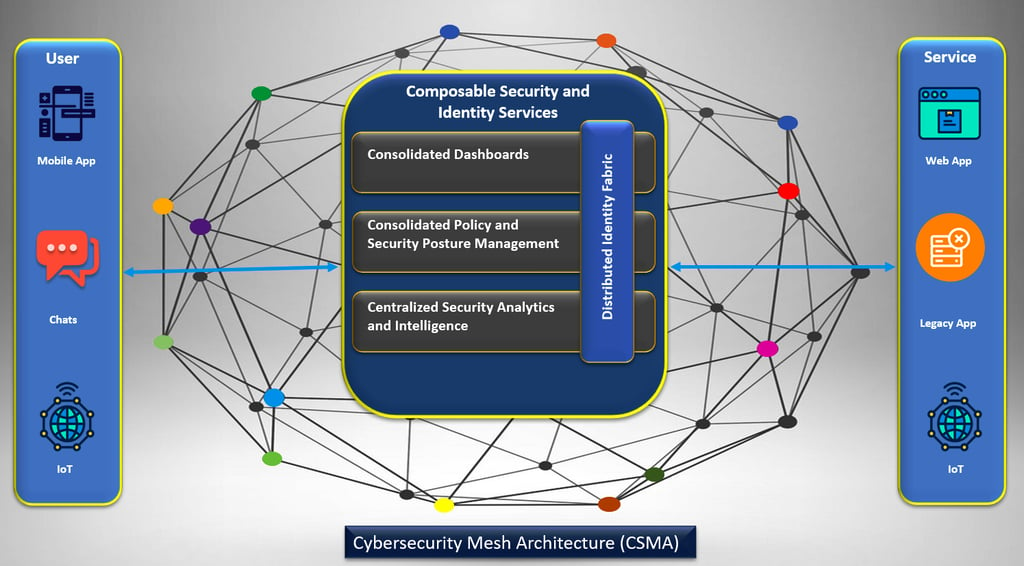
As our existence grows inseparable from digital networks, cyber threats are accelerating at a breakneck pace—outpacing legacy protections and redrawing the boundaries of vulnerability by the hour, a decade ago, protecting a company’s data meant securing a physical office with a firewall. Today, employees work from coffee shops, data lives in the cloud, and smart devices crowd every corner of the network. Traditional security models, built for centralized systems, are like trying to guard a sprawling city with a single lock. Enter Cybersecurity Mesh Architecture (CSMA)—a game-changing approach that’s redefining how businesses stay secure in a borderless digital landscape. Named a top strategic trend by Gartner, CSMA isn’t just a buzzword; it’s the flexible, future-ready shield modern organizations need.
What Exactly Is Cybersecurity Mesh Architecture?
Imagine a security system that acts less like a rigid fortress and more like a team of vigilant neighbors. CSMA ditches the outdated “one-size-fits-all” model for a decentralized approach. Instead of funneling everything through a central hub, it weaves together distributed security tools that collaborate seamlessly—whether your team is logging in from Tokyo, a cloud server in Iowa, or an IoT sensor on a factory floor.
Think of CSMA as a unified safety net. It lets companies enforce consistent security policies across any environment—on-premises, cloud, or edge devices—while integrating tools from multiple vendors. No more siloed systems; just agile, adaptable protection that grows with your needs.
Why Should Businesses Care About CSMA?
Remember when office networks had clear boundaries? Those days are gone. Now, data zips between personal devices, third-party apps, and public clouds, creating a maze that traditional perimeter defenses can’t navigate. Add remote work and IoT sprawl to the mix, and it’s clear why old-school security is struggling.
Here’s where CSMA shines:
Flexibility: It secures assets wherever they are—ideal for hybrid workforces and multi-cloud setups.
Visibility: Offers a bird’s-eye view of threats across the entire digital ecosystem.
Speed: Detects and neutralizes risks faster by connecting the dots between disparate tools.
For example, a bank using CSMA could spot a suspicious login in São Paulo and block it instantly, even if the user’s data is stored in Frankfurt. It’s security that moves at the speed of business.
How Does CSMA Work in Practice?
Let’s break it down without the jargon. CSMA operates like a set of building blocks. Instead of bolting security onto each app or device, it delivers protection as a modular, interconnected service. Key components—like access controls, threat detection, and encryption—communicate through APIs (think of them as universal translators) to create a cohesive defense layer.
Automation supercharges this system. AI analyzes patterns to predict attacks, while orchestration tools let security teams respond with a click. Imagine a self-healing network that patches vulnerabilities before hackers strike—that’s CSMA in action.
The Perks of Going Mesh
Adopting CSMA isn’t just about keeping up; it’s about leaping ahead:
See Threats Coming: Gain real-time insights across all assets, from cloud databases to smart office printers.
Teamwork Makes the Dream Work: Integrate best-in-class tools without vendor lock-in.
Adapt on the Fly: Update security policies dynamically as risks evolve—no manual overhauls needed.
Grow Without Pains: Scale protection effortlessly as your business expands.
But It’s Not All Smooth Sailing
Transitioning to CSMA requires groundwork. Teams might face a learning curve with new tools, and merging legacy systems into the mesh can feel like solving a puzzle. The key? Start small. Pilot CSMA in one department, invest in training, and prioritize tools with open APIs. Remember, this isn’t just a tech shift—it’s a cultural one. Clear communication and patience are vital.
CSMA in the Wild: Who’s Nailing It?
Finance: A global bank used CSMA to secure customer data across 3 cloud platforms, slashing breach response time by 40%.
Healthcare: A hospital network protected patient records with mesh-enabled encryption, breezing through compliance audits.
Manufacturing: A carmaker shielded its IoT-driven factories from ransomware by decentralizing security controls, avoiding costly downtime.
The Bottom Line
As digital landscapes grow more complex, clinging to outdated security models is like using a flip phone in the smartphone era. Cybersecurity Mesh Architecture isn’t just the future—it’s the present. By embracing flexibility, integration, and automation, businesses can turn their security from a bottleneck into a strategic asset.
So, is CSMA worth the hype? Absolutely. In a world where cyber threats never sleep, staying ahead means thinking like a mesh—adaptive, collaborative, and always one step ahead of the game. Ready to future-proof your defenses? The mesh awaits.


